
How Rezonate Maintains Audit-Ready State Using Rezonate - Rezonate

Botanical Ingredient Forensics: Detection of Attempts to Deceive Commonly Used Analytical Methods for Authenticating Herbal Dietary and Food Ingredients and Supplements

Top 10 IT Issues, 2022: The Higher Education We Deserve

Mail Handler - Customers need a product lincense?

Release Notes – Notejoy

Authenticate This LV: READ the rules & use the format in post #1, Page 584

What is a Security Policy? Definition, Elements, and Examples

Query on CMIS Repository #3

Authenticate This LV: READ the rules & use the format in post #1, Page 588

The Recruiter by Douglas London

Configuring IBM i Password Security & Composition Rules for Regulatory Compliance - Seasoft
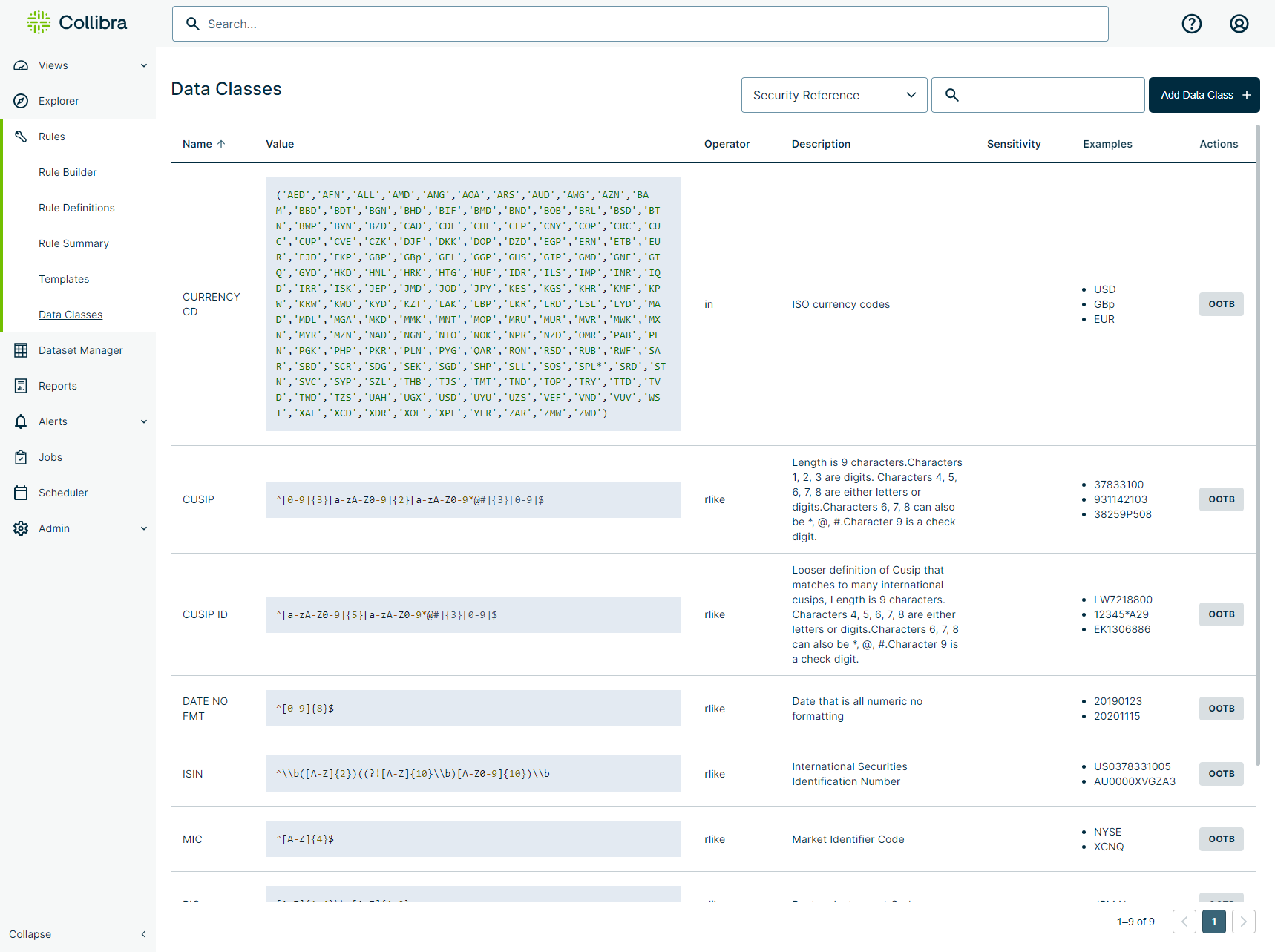
Data Classes

What is DRM? Digital Rights Management Simplified - OTTVerse
